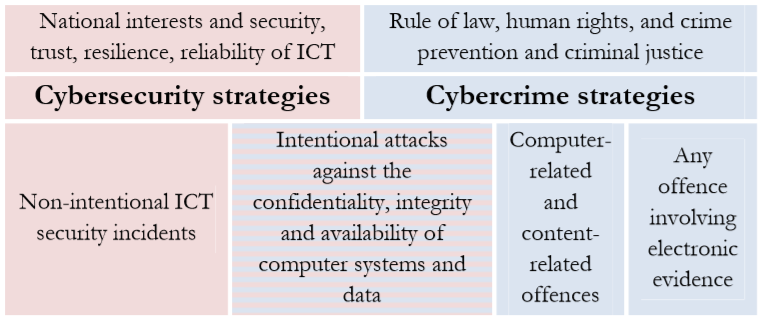
Cybersecurity strategies and cybercrime (or cybercrime prevention) strategies are terms that have been used interchangeably. While cybersecurity and cybercrime strategies complement each other and include some areas of overlap, they are not identical (Seger, 2012) (see Image 1 below). Cybercrime prevention strategies set out the efforts to directly and indirectly deal with cybercrime, such as law enforcement responses and the promotion of national and international cooperation between governments, businesses, academic institutions, organizations, and the public, in order to control and/or reduce cybercrime (Seger, 2012). Put simply, cybercrime strategies focus exclusively on crime prevention and criminal justice policies, programmes, and practices (Seger, 2012). By contrast, cybersecurity strategies provide guidance on cybersecurity matters (which can include cybercrime prevention), and map out objectives, action plans, measures, and the responsibilities of institutions in meeting these objectives. These strategies include legal, procedural, technical, and institutional measures designed to safeguard systems, networks, services, and data.
National cybersecurity strategies elucidate countries' cybersecurity and cybercrime prevention aspirations at the national and international level. These strategies outline the principles on which the strategy is based, prescribe the interests that this strategy seeks to protect, identify the tools used to promote and protect these interests, identify cyberthreats and the challenges these threats pose to national and economic security, delineate cybersecurity policy priorities, and allocate resources to these priorities (Lindstrom and Luiijf, 2012, p. 44). These strategies "encourage … policy-makers to identify strategic objectives ('ends'), to pinpoint the resources available to reach those objectives ('means'), and to provide a guide on how such resources are to be applied to reach stated objectives ('ways')" (Lindstrom and Luiijf, 2012, p. 46).
Cybersecurity strategies detail why the strategy is important and why it is needed ( context), what it does ( objectives), what it covers, and what and whom it impacts ( scope) (ITU, 2018, p. 30). Key components of these strategies are objectives, priority actions, expected outcomes, and evaluation mechanisms.
The objectives of cybersecurity strategies include national security-related objectives and information and communication technology-related objectives. For instance, Sweden's cybersecurity "strategy is based on the objectives for Sweden's security: protecting the lives and health of the population, the functioning of society, and …[its] capacity to uphold fundamental values such as democracy, the rule of law and human rights and freedoms. … The strategy is also based on the overall [information technology (IT)] … policy objective - for Sweden to become the world leader in harnessing the opportunities of digital transformation" (Swedish Ministry of Justice, 2017, p. 1; see also Swedish Ministry of Justice, " A National Cyber Security Strategy "). In Nigeria, the objectives of their Cybersecurity Strategy (2014) are as follows (Section 3.3.2):
The priority actions are designed to achieve these objectives. In the European Union, for example, the majority of national cybersecurity strategies identify the creation of cybersecurity standards, norms, and laws (wherever needed), the fostering of a cybersecurity culture not only among relevant stakeholders (i.e., government agencies, academic institutions, businesses, and organizations) but also the general public, and the cultivation of national and international cooperation and collaboration between relevant stakeholders, as priority actions (ENISA, 2014). Some priority actions listed in the US National Cyber Strategy of 2018 are to "prioritize innovation;" "encourage universal adherence to cyber norms;" "lead with objective, collaborative intelligence;" and "improve apprehension of criminals located abroad" (to name a few).
The expected outcomes of these priority actions include what should be achieved as a result of these actions (e.g., the development of cybersecurity standards). For example, the US National Cyber Strategy of 2018 lists expected outcomes as the effective management of cybersecurity vulnerabilities; the reduction or prevention of "destructive, disruptive, or otherwise destabilizing malicious cyber activities directed against United States interests," and the deterrence of "activity that is contrary to responsible behaviour in cyberspace … through the imposition of costs through cyber and non-cyber means;" and the ability of the United States "to use cyber capabilities to achieve national security objectives" (US White House, 2018, p. 3).
The evaluation mechanisms include the tools that can be used to determine what has actually been achieved (and by way of extension, how this compares with the expected outcomes). Key performance indicators (KPIs), which are measures that are used to determine progress towards the realization of the strategic objectives of the national cybersecurity strategy (ENISA, n.d., Annex B), are also included. Based on this evaluation, the national security strategies are amended and priority actions revised (ITU, 2018).
Exemplar cybersecurity strategies include the appropriate policy instruments (e.g., standards, policies, laws, education programmes, etc.) needed to achieve the objectives of these strategies (ITU, 2018, p. 33), and those responsible for overseeing the implementation of these instruments. For example, in its National Cybersecurity Policy 2017-2022, Chile includes the measures that should be implemented based on specific strategic objectives and the agencies responsible for implementing and/or assisting in the implementation of these measures. Likewise, the Philippines National Cybersecurity Plan 2022, identifies measures to achieve strategic objectives and the roles and responsibilities of key stakeholders.