The International Telecommunications Union ( ITU), a United Nations agency that is considered the "premier global forum through which parties work towards consensus on a wide range of issues affecting the future direction of the ICT industry" (ITU, n.d.), launched the Global Cybersecurity Agenda , which is "a framework for international cooperation aimed at enhancing confidence and security in the information society" (ITU, n.d.). The ITU Global Cybersecurity Agenda identifies five strategic pillars: legal, technical, organizational, capacity-building, and cooperation (see Image 3).
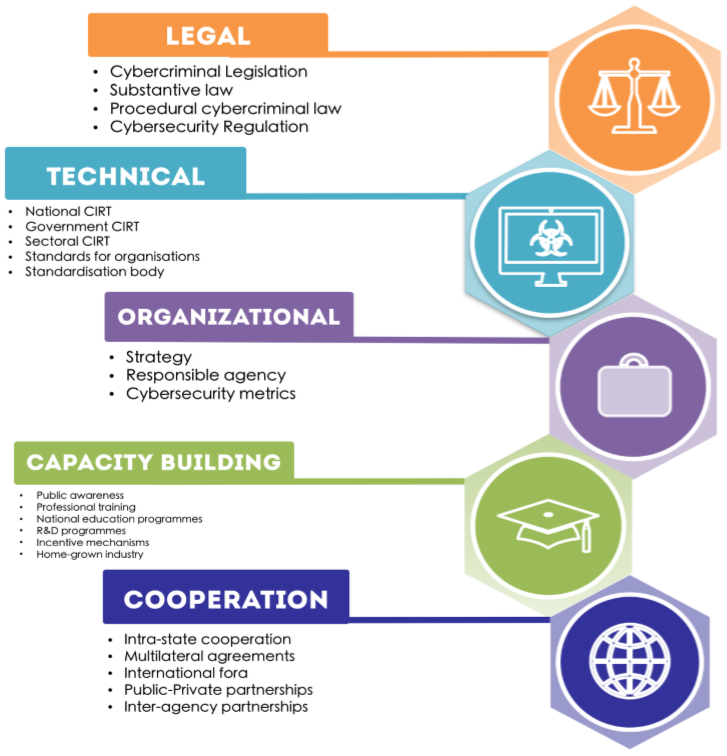
The legal pillar focuses on harmonized regulations and laws relating to cybersecurity and cyber-dependent and cyber-facilitated crimes. Cases in point are cybercrime laws (see Cybercrime Modules 2 and 3), data protection laws and regulation (see Cybercrime Module 10), cybersecurity laws, and other related laws (e.g., Denmark, Danish Data Protection Act of 2018; Fiji, Crimes Decree 2009: Division 6 - Computer Offences; and United Arab Emirates, Federal Law No. (1) of 2006 on Electronic Commerce and Transactions; and the United Kingdom, Computer Misuse Act of 1990 and Data Protection Act of 2018. For more information about this pillar, see ITU, 2015; ITU, 2017).
The technical pillar covers existing technical institutions, cybersecurity standards and protocols, and the measures needed to deal with cybersecurity threats. An example of a technical institution is a Computer Emergency Response Team (CERT), which is defined as "an organization or team that provides, to a well-defined constituency, services and support for both preventing and responding to computer security incidents" (Wahid, 2016). CERTs vary in capabilities depending on the range and combination of reactive, proactive and/or security quality management services offered (CMU-SEI, 2006). For example, these services can include promptly responding to an incident so that the attack can be quickly contained and investigated, and to facilitate rapid recovery to a pre-incident state (Borodkin, 2001). In addition to incident response, a CERT may engage in other activities, such as conducting vulnerability assessments and providing security briefings; these additional activities depend on the organization (Proffitt, 2007). Countries can have national, government, and sector-specific CERTs and Computer Security Incident Response Teams (or CSIRTs), or a combination of some or all of these (for more information about this pillar, see ITU, 2015; ITU, 2017). CERTs/CSIRTs have also created groups within their regions to share information and coordinate activities, among other things (e.g., Asia-Pacific CERT or APCERT; Africa CERT or AfricaCERT).
CERT® is a registered trademark of the Software Engineering Institute of Carnegie Mellon University. CSIRTs can request authorization to use the CERT mark. This website includes the steps that should be taken by a CSIRT to receive authorization to use the CERT mark.
The organizational pillar includes organizational structures and policies on cybersecurity and responsible agencies for coordinating cybersecurity policy. National cybersecurity strategies and national cybersecurity frameworks are included in this pillar, as well as the regulatory bodies that oversee the implementation of these strategies and frameworks (e.g., the Cyber Security Council in Iceland; the Federal Office for Information Security in Germany; the Office of Cybersecurity and Information Assurance in the United Kingdom; the Ministry of Science, ICT and Future Planning in the Republic of Korea; and the National Planning Department and the Ministry of Information Technologies and Communications in Colombia, to name a few (for more information about this pillar, see ITU, 2015; ITU, 2017).
The capacity-building pillar covers efforts to promote cybersecurity awareness, education and training. Examples include public awareness campaigns, cybersecurity research and development, professional training, and national education programmes and curricula. For example, in the Dominican Republic, "[t]he National Commission for Information Society and Knowledge (CNSIC) has an officially recognized national awareness program that promotes norms, values and social behaviours that contribute to integrity, creativity and innovation in navigating cyberspace" (ITU, 2015, p. 171; for more information about this pillar, see ITU, 2015; ITU, 2017). Related cybersecurity awareness and education campaigns have been launched by other countries as well (see box on "Examples of National and InternationalCybersecurity Awareness and Education Campaigns"). In addition to these cybersecurity awareness and education campaigns, the ITU provides tools to assist countries in their capacity building efforts. These tools are designed to "capture information about specific threats targeting the country" (Honeypot Research Network or HORNET ) and "aggregate and disseminate relevant incident data" (Abuse Watch Alerting and Reporting Engine or AWARE ) (ITU, n.d.).
CyberBayKin, a Myanmar Cyber Security Campaign, was launched in 2018 to raise awareness about cyber safety and risk in Myanmar. It is initiated by Monash University (Australia) and Kernellix Co., Ltd. (Myanmar), in collaboration with the Myanmar Ministry of Transport and Communications National Cyber Security Centre. Six Myanmar comic characters have been designed for the campaign are introduced at the launch. The year-long campaign will see fortnightly cybersecurity awareness comic illustrations appear on the campaign facebook platform. It is supported and funded by the Australian Department of Foreign Affairs and Trade under the International Cyber Engagement Strategy and the School of Social Sciences at Monash University (CyberBayKin, 2018).
The cooperation pillar focuses on inter-agency and public-private partnerships, information sharing networks, and cooperative agreements. A case in point is Australia's International Cyber Engagement Strategy to enhance public-private collaboration and collaboration between countries. Other examples include countries' partnerships and information exchange with the ITU, European Union Agency for Network and Information Security (ENISA), Organization for Security and Co-operation in Europe (OSCE), and North Atlantic Treaty Organization (NATO), and cooperative agreements, such as the Council of Europe's Convention on Cybercrime of 2001, Commonwealth of Independent States' Agreement on Cooperation in Combating Offences related to Computer Information of 2001, the League of Arab States' Arab Convention on Combating Information Technology Offences of 2010, and the African Union Convention on Cyber Security and Personal Data Protection of 2014, to name a few (for more information about this pillar, see ITU, 2015; ITU, 2017).
A comparative analysis by the Organisation for Economic Co-operation and Development (OECD) (2012) of national cybersecurity strategies in ten countries (Australia, Canada, Finland, France, Germany, Japan, the Netherlands, Spain, the United States, and the United Kingdom), revealed differences in definitions of cybersecurity, but similarities in the countries' approaches to dealing with cybersecurity in a comprehensive manner, by including content from each legal, technical, organizational, capacity building, and cooperation pillar to varying degrees.
To create a comprehensive and effective national cybersecurity strategy, the 2018 ITU Guide to Developing a National Cybersecurity Strategy proposes the inclusion of the following thematic areas in the strategy: governance (discussed in this Module); risk management (i.e., the process of identifying, evaluating, and controlling and/or eliminating threats; discussed in Cybercrime Module 9); preparedness and resilience (discussed in Cybercrime Module 9); critical infrastructure services and essential services (discussed in Cybercrime Module 14); capacity and capacity building and awareness raising (discussed in this Module and Cybercrime Module 7); legislation and regulation (discussed in Cybercrime Modules 2, 3 and 10); and international cooperation (discussed in Cybercrime Module 7). Other organizations have also provided guidance on the development of cybersecurity policy and regulatory frameworks, technical and organizational measures, capacity building, and cooperation (e.g., the Commonwealth Telecommunications Organization's Commonwealth Cybergovernance Model of 2014).