Cyber organized crime can include organized criminal groups engaging in cybercrime and cybercriminals or other groups that do not meet the criteria established by the Organized Crime Convention, that engage in activities typically associated with organized crime. Regarding the first type of cyber organized crime, there is evidence that traditional organized criminal groups have engaged in cybercrime (UNODC, 2013; UNODC, 2012). Studies have also shown that organized criminal groups have exploited the opportunities afforded to them by information and communication technology to commit cybercrime. Specifically, research has shown that organized criminal groups have utilized information and communication technology to exploit new online criminal markets (e.g., Internet gambling) (Wang and Antonopoulos, 2016; Kshteri, 2010). For example, in 2016, members of Camorra and 'Ndrangheta were arrested for their role in an Internet gambling ring (OCCRP, 2016; Reuters, 2016). What is more, organized criminal groups have also engaged in cybercrime to facilitate offline organized crime activities. For example, an organized criminal group that trafficked drugs hired hackers to gain access to the information technology systems of the Antwerp port in Belgium that housed data about containers (Bateman, 2013; Glenny, 2017).
Organized criminal groups engaging in cyber organized crime may or may not exclusively operate in cyberspace. In fact, studies have expanded the notion of organized crime to include activities driven by some direct or indirect benefit that occur in whole or in part online (Grabosky, 2007; Broadhurst, et al., 2014). These groups can thus operate either partially, predominately, or solely online. While there have been cases of networks that have been formed and/or operated exclusively and/or predominantly online (e.g., Shadowcrew ; for information about these types of networks, see Leukfeldt, Kleemans, and Stol, 2017; Leukfeldt, Kleemans, and Stol, 2016a; Leukfeldt, Kleemans, and Stol, 2016b, Choo and Smith, 2008; and Choo, 2008), research on the creation and development of cyber organized criminal networks have shown that geographic proximity and offline contacts play a large role in the formation and expansion (through recruitment) of these networks (Broadhurst et al., 2014; Leukfeldt, Kleemans, and Stol, 2017; Leukfeldt, Lavorgna, and Kleemans, 2017, pp. 292-293). For example, hot spots and hubs for cyber organized criminal networks have been identified in Eastern Europe (Bhattacharjee, 2011; Kshetri, 2013; Broadhurst et al., 2014, p. 3). Furthermore, Europol (2018) revealed that "social engineering scams targeting EU citizens are carried out by West African organized crim[inal] groups" (p. 13).
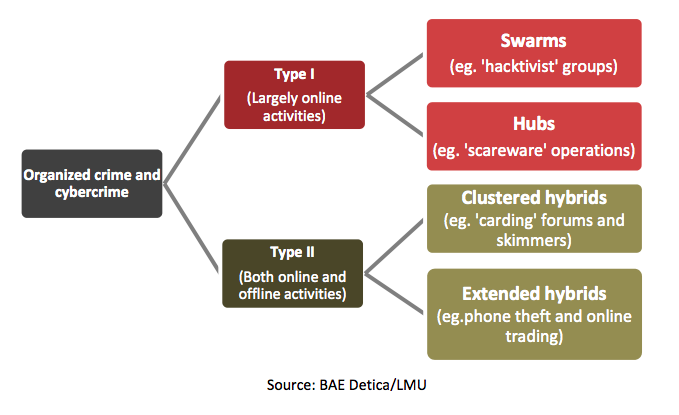
The extent of organization of cyber organized crime is still largely unknown (Lavorgna, 2016). Empirical evidence of the structure of cyber organized crime, groups involved in this type of cybercrime, and the types of cybercrimes committed, is sparse (UNODC, 2013, p. 45). Nevertheless, typologies have been created based on available data concerning the links between organized crime and cybercrime based on "the degree of involvement of groups in online (as opposed to offline) activities and the structure of associations within the group" (BAE Systems Detica and London Metropolitan University, 2012, cited in UNODC, 2013, p. 46). Particularly, three general types of groups were identified: groups that predominantly operate online and commit cybercrimes (Type I); those that operate offline and online and engage in crimes and cybercrimes (Type II) (see Image 1); and those only utilizing information and communication technology to facilitate offline crimes (Type III; not depicted in Image 1).
Source: Image obtained from UNODC (2013). Draft Comprehensive Study on Cybercrime . p. 46.
A further distinction is made between each type of group (BAE Systems Detica and London Metropolitan University, 2012; UNODC, 2013; Broadhurst et al., 2014):
Certain criminalgroups that engage in cyber organized crime challenge traditional notions of organized crime. Consider, for example, the definition of organized crime included in the United Nations Convention against Transnational Organized Crime. The definition includes the requirement that the group exist "for a "period of time;" however, this period is not defined in the Convention and the interpretation of "period of time" has varied. On the other hand, the group does not need continuity of its membership. In view of that, would a swarm meet this requirement?
Individuals within these groups have various roles and levels of importance within these groups. Some individuals are considered essential to the group and its operations, while others are considered non-essential, maybe even expendable. The former includes the leader and some core members that are vital to the success of the group's activities, which depends on the cybercrime (or cybercrimes) committed (e.g., programmers, intrusion specialists, technical experts, data miners, and money specialists, to name a few) (National Cyber Security Centre, 2017, pp. 5-6; UNODC, 2013, p. 46). The latter has been observed, for example, with money mules. These individuals (knowingly or unknowingly) are recruited by and work for criminals, transfer goods between third parties, and have been used to launder money (Maras, 2016).
In 2018, a criminal group that engaged in cyber organized crime was involved in a business email compromise attack (similar to spearphishing and whaling; discussed in Cybercrime Module 2 on General Types of Cybercrime), which tricked the targets into wire transferring money to the perpetrators of this cybercrime who were masquerading as legitimate entities that the companies worked with (see Operation Wire Wire, FBI, 2018). In this incident, money mules within the United States were offered a job to conduct wire transfers and/or were recruited to create shell companies and open up bank accounts for the shell companies to receive the proceeds of the online fraud. Once the money was transferred into the bank accounts controlled by the money mule, the money mule kept a portion of the proceeds (agreed upon with their recruiter and/or members of the group) and transferred the money to a bank in Poland or China (Neil, 2018). Money mules, and other non-core members of cybercriminal groups engaging in organized crime activities, are transient, participating in the activities of the group only as needed and/or until they fulfil their purpose.
Cyber organized criminals deployed Koobface (an anagram for Facebook), a computer worm designed to spread via social media platforms. This malware spread by sending messages via social media to users from their friends' infected accounts. This message would have a link to a video. When users would click on the link in the message, they were led to a website with the video. Once at that site, the users were prompted to download an update or video codec in order to see the video, which was actually the malware. The malware had many different functions, among them were its ability to harvest data and license keys from infected systems, redirect Internet traffic for profit, and download content to users' systems.
For more information see: Richmond, Riva (2012). Web Gang Operating in the Open. New York Times, 16 January 2012.
Case law has revealed that cybercriminals and/or members of organized criminal groups that engage in cybercrime have been charged with offences used to prosecute organized criminals. For example, in the United States, active members of online illicit markets (e.g., Carders.su, AlphaBay) have been charged with conspiracy or racketeering offences. Conspiracy constitutes participation in an organized criminal group, according to the United Nations Convention against Transnational Organized Crime. Racketeering is initially a common law offence (see Module 2 of the Teaching Modules Series on Organized Crime).
Online illicit markets (or dark markets) have been considered a criminal enterprise, "a group of individuals with an identified hierarchy, or comparable structure, engaged in significant criminal activity" (FBI, n.d.). Online forums, such as the now defunct AlphaBay, DarkMarket, Darkode, and Carder.su, have clearly defined hierarchies (administrators, moderators, and ranking of members based on privileges) (Maras, 2016). Individuals seeking to gain access to these forums had to have existing members recommend them (ICE, 2017). The same holds true for other defunct online illicit markets. A case in point is Silk Road, an infamous darknet site (now defunct) that primarily sold illicit drugs and was also considered a criminal enterprise. The administrator of the site, Ross Ulbricht, obtained a percentage of every sale, tightly regulated and controlled the activity on the site, utilized moderators to monitor and enforce the rules of the site, and acted if those rules were not followed ( United States v. Ross William Ulbricht; 2016; Maras, 2016). This enforcement of rules is essential as the success of dark markets essentially depends on "trust [which] is critical when relying on others in high risk and vulnerable situations to deliver goods and services, especially when the transactions are illicit in nature. Victims of non-delivery or counterfeit items cannot report this to the police, because they have engaged in unlawful conduct" (Maras, 2016, p. 344).
The US prosecution of Ross William Ulbricht brought worldwide attention to the darknet and the illicit actives occurring within this space.
Read:
For similar cases visit UNODC's SHERLOC Portal.